Make sense of complicated security documents, turning them into clear and useful information. Our team uses modern tools to check and improve your security measures, making sure your data is safe from new threats.

Risk Assessment

Security Audits

Benchmarking

We help to see future financial risks before they happen and plan your security better. Our consulting helps you protect your investments by spotting and handling risks early with smart, safe strategies.

Data Protection Strategies

Compliance Guidance


Our services don’t just protect your IoT devices; they also create engaging stories that explain and persuade effectively. This makes sure your IoT setups are safe and easy for people to use and understand.

Device Authentication

Encryption


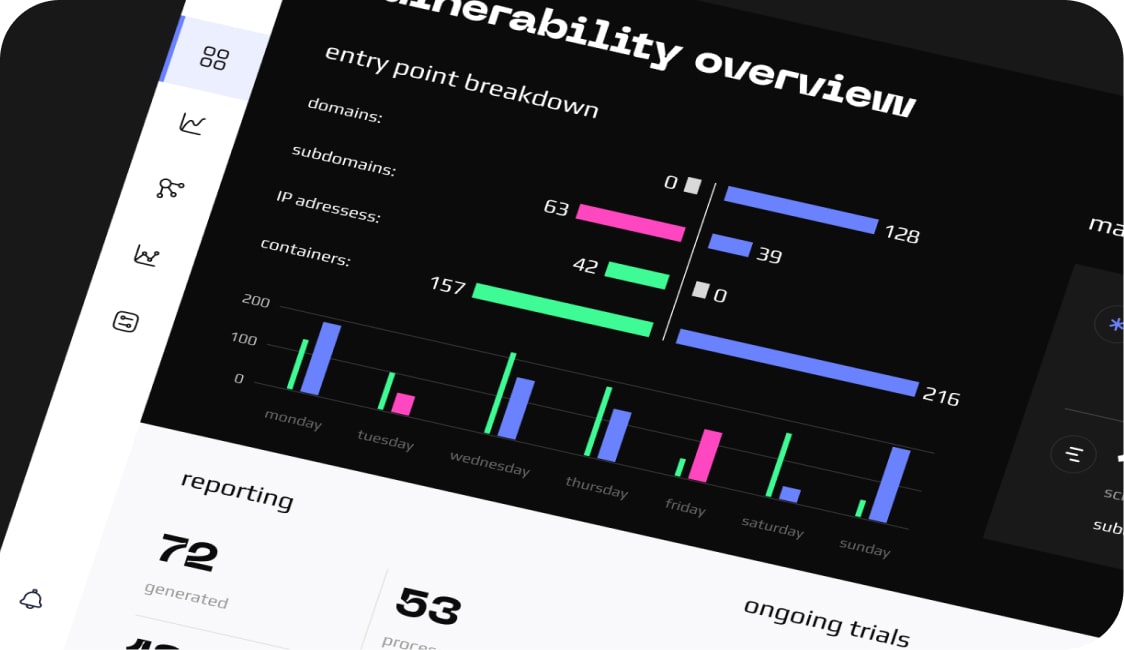
We really understand your systems and find weak spots by acting like cyber attackers. This helps us find and fix security holes, keeping your customer information very safe.

Simulated Cyber Attacks

Reporting

Remediation Support


We keep your network safe from DDoS attacks, which try to shut down your service. It predicts these attacks and stops them, making sure your business runs smoothly and always delivers products on time.

Traffic Analysis

Rate Limiting

Redundancy and Scalability